There are many different types of VPNs out there. Wondering which type is right for you? iFixApple can help you understand the differences between them and help you choose the best VPN for your needs.
The truth is virtual private networks come in many different shapes. It can be overwhelming to distinguish between the technologies used, let alone understand which type is the optimal choice for your needs.
Allow us to help you out! We’ll try to give you a concise, informative overview of the important variables that divide virtual private networks into several categories – from environment and setup to protocols and features.
VPNs can be divided into three main categories – remote access, intranet-based site-to-site, and extranet-based site-to-site. Individual users are most likely to encounter remote access VPNs, whereas big businesses often implement site-to-site VPNs for corporate purposes.
Let’s take a closer look at the different types.
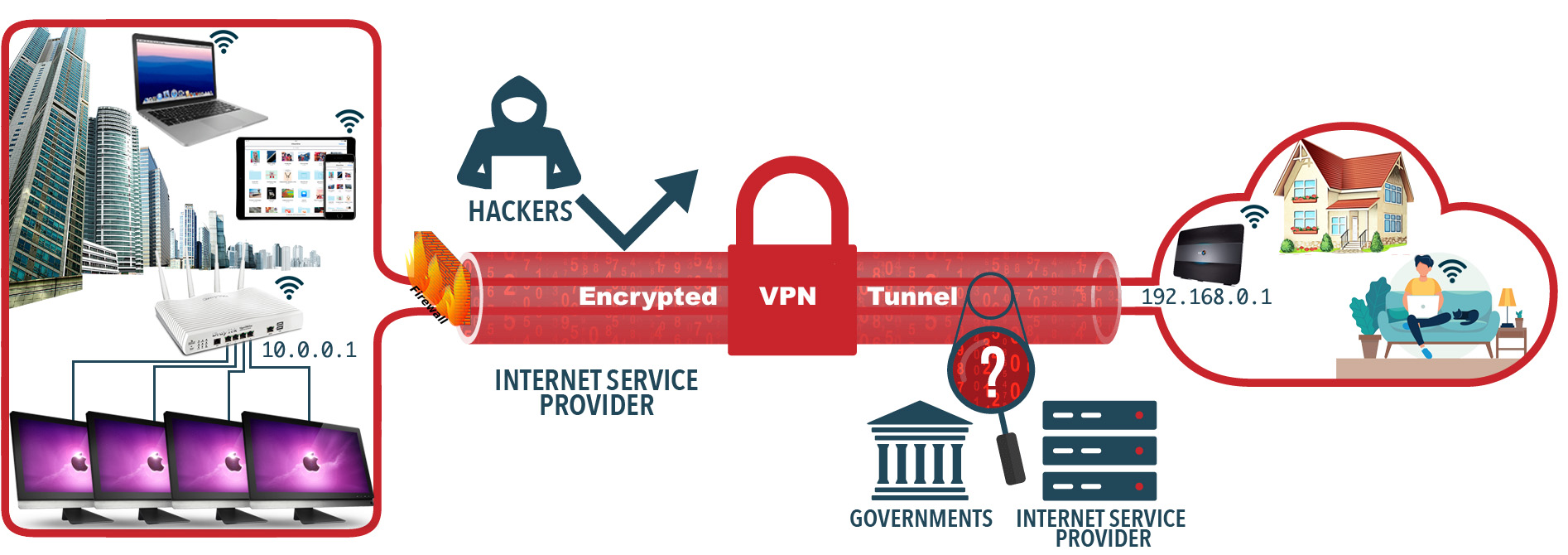
A Remote access VPN allows individual users to establish secure connections with a remote computer network. This is the foundation upon which the so-called commercial VPN services are built. Those users can access the secure resources on that network as if they were directly plugged in to the network's servers. An example of a company that needs a Remote Access VPN is a firm with salespeople in the field or have staff working from home. Another name for this type of VPN is virtual private dial-up network(VPDN), acknowledging that in its earliest form, a remote-access VPN required dialing in to a server using an analog telephone system.
There are two components required in a remote-access VPN. The first is a Network Access Server "NAS" also called a media gateway or a Remote-Access Server "RAS". (Note: IT professionals also refer to NAS meaning Network Attached Storage.) A NAS might be a dedicated server, or it might be one of multiple software applications running on a shared server. It's a NAS that a user connects to from the internet in order to use a VPN. The NAS requires that user to provide valid credentials to sign in to the VPN. To authenticate the user's credentials, the NAS uses either its own authentication process or a separate authentication server running on the network.
The other required component of remote-access VPNs is client software. In other words, employees who want to use the VPN from their computers require software on those computers that can establish and maintain a connection to the VPN. Most operating systems today have built-in software that can connect to remote-access VPNs, though some VPNs might require users to install a specific application instead. The client software sets up the tunneled connection to a NAS, which the user indicates by its internet address. The software also manages the encryption required to keep the connection secure.
The main benefits of remote access VPNs are fairly easy to setup and hassle-free to use. With the right software, this type of VPN can be easily accessible to newcomers and veterans alike, and is ideal for personal use. However, it may be unsuitable or even incompatible with large-scale business needs.
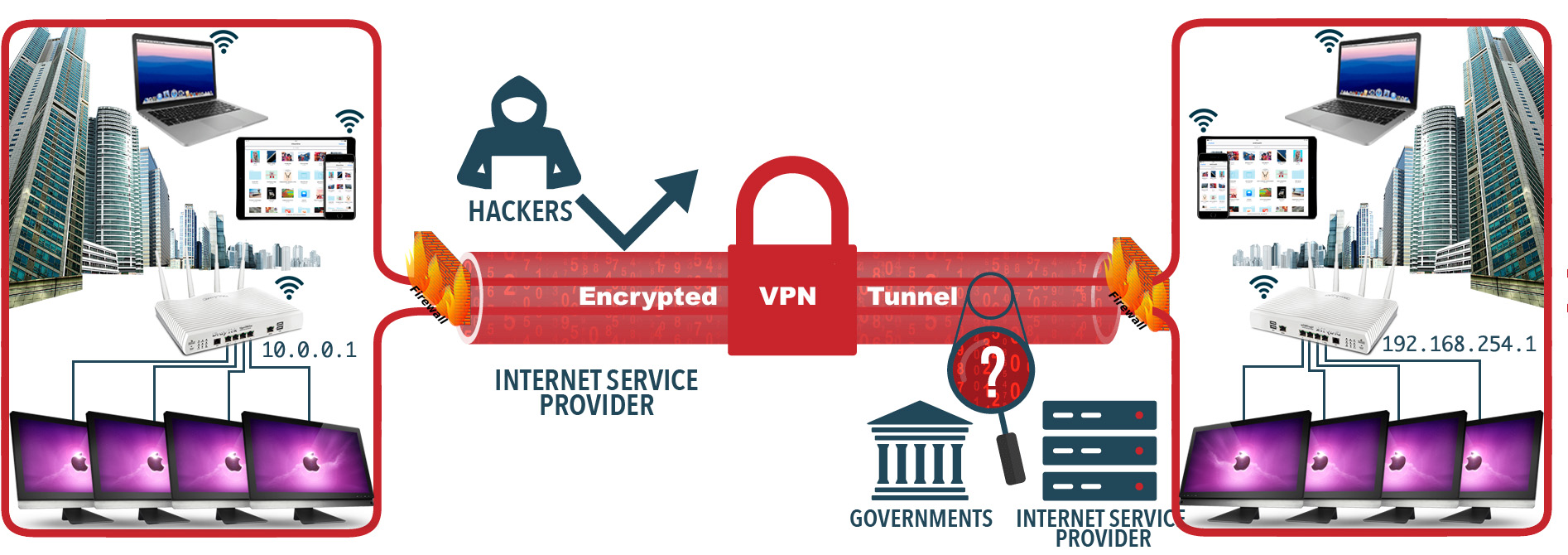
Site-to-site VPNs work in a different manner – the main goal is to provide multiple users in various locations with the ability to access each other’s resources.
for example: you’re working in the London branch of a company, and you’re currently working with employees from the New York branch. Thanks to the site-to-site VPN, your local area networks (LANs) are both connected to the same wide area network (WAN) – in other words, you can securely share the information and resources like printers and servers etc. between each other. this is an example of an intranet-based site-to-site VPN. The other type is extranet-based, and is used when a company has a close relationship with another company (such as a partner, supplier or customer), it can build an extranet VPN that connects those companies' LANs. This extranet VPN allows the companies to work together in a secure, shared network environment while preventing access to their separate intranels..
The above two VPN types are based on different VPN security protocols. Each of these VPN protocols offer different features and levels of security, and are explained below:
 Internet Protocol Security or IPSec is used to secure Internet communication across an IP network. IPSec secures Internet Protocol communication by authenticating the session and encrypts each data packet during the connection. IPSec operates in two modes, Transport mode and Tunnelling mode, to protect data transfer between two different networks. The transport mode encrypts the message in the data packet and the tunnelling mode encrypts the entire data packet. IPSec can also be used with other security protocols to enhance the security system.
Internet Protocol Security or IPSec is used to secure Internet communication across an IP network. IPSec secures Internet Protocol communication by authenticating the session and encrypts each data packet during the connection. IPSec operates in two modes, Transport mode and Tunnelling mode, to protect data transfer between two different networks. The transport mode encrypts the message in the data packet and the tunnelling mode encrypts the entire data packet. IPSec can also be used with other security protocols to enhance the security system.
 L2TP or Layer 2 Tunnelling Protocol is a tunnelling protocol that is usually combined with another VPN security protocol like IPSec to create a highly secure VPN connection. L2TP creates a tunnel between two L2TP connection points and IPSec protocol encrypts the data and handles secure communication between the tunnel.
L2TP or Layer 2 Tunnelling Protocol is a tunnelling protocol that is usually combined with another VPN security protocol like IPSec to create a highly secure VPN connection. L2TP creates a tunnel between two L2TP connection points and IPSec protocol encrypts the data and handles secure communication between the tunnel.
 PPTP or Point-to-Point Tunnelling Protocol creates a tunnel and encapsulates the data packet. It uses a Point-to-Point Protocol (PPP) to encrypt the data between the connection. PPTP is one of the most widely used VPN protocol and has been in use since the time of Windows 95. Apart from Windows, PPTP is also supported on Mac and Linux.
PPTP or Point-to-Point Tunnelling Protocol creates a tunnel and encapsulates the data packet. It uses a Point-to-Point Protocol (PPP) to encrypt the data between the connection. PPTP is one of the most widely used VPN protocol and has been in use since the time of Windows 95. Apart from Windows, PPTP is also supported on Mac and Linux.
 SSL (Secure Sockets Layer) and TLS (Transport Layer Security) create a VPN connection where the web browser acts as the client and user access is restricted to specific applications instead of entire network. SSL and TLS protocol is most commonly used by online shopping websites and service providers. Web browsers switch to SSL with ease and with almost no action required from the user, since web browsers come integrated with SSL and TLS. SSL connections have https in the beginning of the URL instead of http.
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) create a VPN connection where the web browser acts as the client and user access is restricted to specific applications instead of entire network. SSL and TLS protocol is most commonly used by online shopping websites and service providers. Web browsers switch to SSL with ease and with almost no action required from the user, since web browsers come integrated with SSL and TLS. SSL connections have https in the beginning of the URL instead of http.
 OpenVPN is an open source VPN that is useful for creating Point-to-Point and Site-to-Site connections. It uses a custom security protocol based on SSL and TLS protocol and is one of the most used protocols. It is an open-source protocol that uses encryption based on the OpenSSl and SSLv3/TLSv1 protocols. Most VPN providers support OpenVPN and it is available for a lot of different platforms (e.g. Windows, Mac (OSx), Android, iOS, Linux, routers). Most consider OpenVPN to be the best choice.
OpenVPN is an open source VPN that is useful for creating Point-to-Point and Site-to-Site connections. It uses a custom security protocol based on SSL and TLS protocol and is one of the most used protocols. It is an open-source protocol that uses encryption based on the OpenSSl and SSLv3/TLSv1 protocols. Most VPN providers support OpenVPN and it is available for a lot of different platforms (e.g. Windows, Mac (OSx), Android, iOS, Linux, routers). Most consider OpenVPN to be the best choice.
 Secure Shell or SSH creates the VPN tunnel through which the data transfer happens and also ensures that the tunnel is encrypted. SSH connections are created by a SSH client and data is transferred from a local port on to the remote server through the encrypted tunnel.
Secure Shell or SSH creates the VPN tunnel through which the data transfer happens and also ensures that the tunnel is encrypted. SSH connections are created by a SSH client and data is transferred from a local port on to the remote server through the encrypted tunnel.
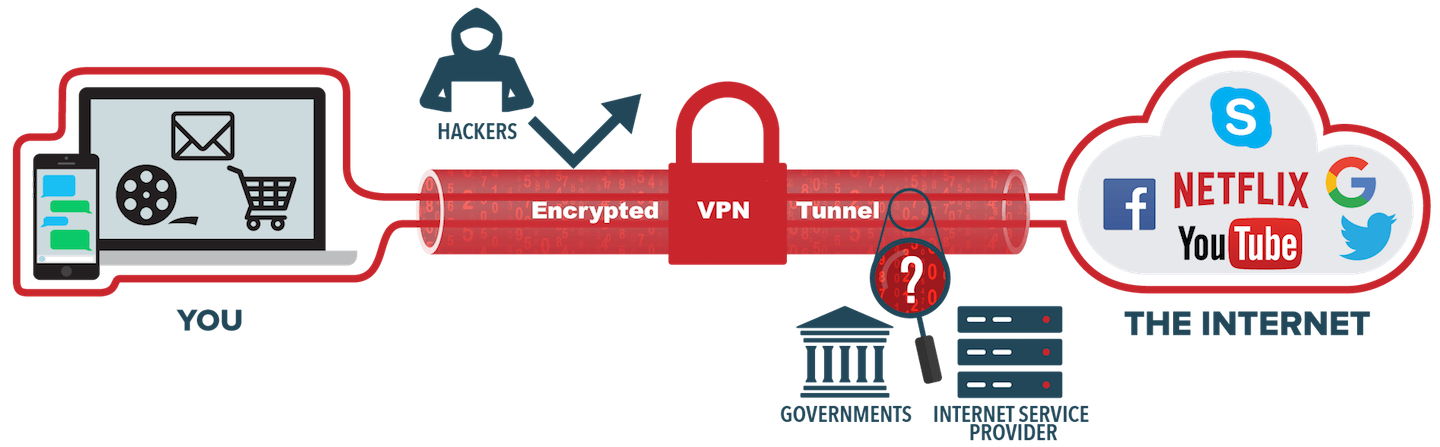
This type of VPN creates a secure connection between you and the internet. When you connect to the internet through a VPN, all your data traffic is sent through an encrypted virtual tunnel. This has multiple advantages:
As with anything free, there is ultimately a catch or a limit placed upon it:
If you only require the advantages of a VPN occasionally, a freebie version is adequate, but for those in need of more, a commercial version is always the best.
1. Any deals on the cheap side potentially have no taxes added to the price, the discounted amount will only apply to the first billing period and it will automatically renew on your credit card. The features may also be limited. Always check the fine print, before handing over your credit card details or better yet use PayPal if possible, so it’s easy to check and cancel the subscription yourself.
2. Ensure that the plan has servers in the countries and regions that you need. Performance is not guaranteed by having a large number of servers in a particular country, even though the load can be spread around.
3. Look into how many simultaneous connections are supported. Usually, it’s from three to five, allowing you to have a mobile, a tablet, and a PC connected at the same time. Again, read the fine print, as most plans have fair usage policies to stop people from hogging resources and it’s for a single user only.
4. Occasionally providers list the connection protocols such as OpenVPN and IKeV2, that are fast and secure. Others may include SSTP, PPTP, TCP, and UDP for OpenVPN. You can be a bit of a dummy in this regard, but choices can make the service faster or give more reliable connections.
5. Always check the Privacy Policy and Terms of Service to find out what data the provider collects and for how long the information is stored. Some record when you log on, the amount of data used and delete everything else when you close the session. Others may add your incoming IP address and server used, keep the data for months, maybe even years and heaven forbid share the information with others. Check on any restrictions about who can sign up; you may have to be over 18. The service may stipulate that it’s only for non-commercial or personal use.
6. When you find the VPN that suits your purposes, always trial it if possible before committing yourself long term.
 VPN software is available on most mobile platforms, but they’re not always for use with every possible brand and scale of firewall.
VPN software is available on most mobile platforms, but they’re not always for use with every possible brand and scale of firewall.
The lines become blurred here: the big software players tend to mix connectivity (traditional VPN) with management (remotely erasing a phone or tablet, for example) in a giant blancmange of services. Perhaps it’s best to remember that SSL is the lowest common denominator for many tablet and phone devices when it comes to VPN transport.

The legality of VPNs is a cloudy issue and depends on where you are physically sitting when using a VPN. Generally speaking in many countries, VPNs are legal.
While virtual private networks may conjure images of illegal activities and mysterious figures on the dark web, in reality VPNs are currently legal to use in many countries, including the U.K. Some VPN's encrypt your connection to the internet, disguise your IP address, and prevent others, like the government or internet service providers (ISPs), from tracking your virtual whereabouts.
There are plenty of legitimate reasons to want this degree of privacy, but you should understand what’s considered legal and illegal while using a VPN.* It is the responsibility of VPN users to identify whether their use of a VPN is legal (or not), and to check their country’s laws before using a VPN.
Below is a list of some countries where the government controls VPNs:
VPNs are banned in:
For particular details of each country (whether you may be fined or thrown into prison), you should check out the latest developments. Some countries with severe restrictions on the use of VPNs are only relevant to its residents, not for a tourist who may happen to be using a VPN to secure a hotel Wi-Fi.
Using a VPN in the U.K. is currently legal. However, if you use a VPN to commit an act that is illegal without a VPN, it is still illegal when using one. That may include downloading and selling copyrighted information, hacking into computers or networks without authorisation, and cyberstalking. Additionally, using a VPN to circumvent a website’s or app’s technological protection measures (such as geo-locking) could violate the law in some countries, as well as the VPN’s and the website’s Terms and Conditions.
Here’s the thing: there are many different types of VPNs, and the right one for you can range from a budget pick with basic functionality for casual use, to an advanced and feature-rich service that has to excel in multiple categories. In other words, the answer to the question “what is the perfect VPN for you?” depends heavily on your needs and expectations.
Even if you have a clear idea of your requirements, choosing a reliable service that performs as well as it advertises itself can be a challenge, between the countless VPNs available today.
We can help with that. Contact iFixApple and we can advise your many options for being able to work remotely. from simple port forwarding using you current router with no additional hardware required or subscriptions to a fully secure, both locally and remotely firewall / NAS appliance. there are MANY options depending on your various needs as to the type of VPN you require! We can install and configure whatever your needs.